Changelog
Follow up on the latest improvements and updates.
RSS
improved
fixed
Mac Roaming Client
RC Release Channels
April 22, 2024 macOS RC 1.8.2 Production Release
A new version of the macOS RC is now available in Production release channel for New Installs. This version can be downloaded from the dashboard
Deployments
→ Roaming Clients
→ Install.
Auto-update rollout will begin this week with 5% rollout, please refer to our release status page for the latest available versions in both Beta and Production channels.
Included in macOS v.1.8.2
Improvements 🛠️
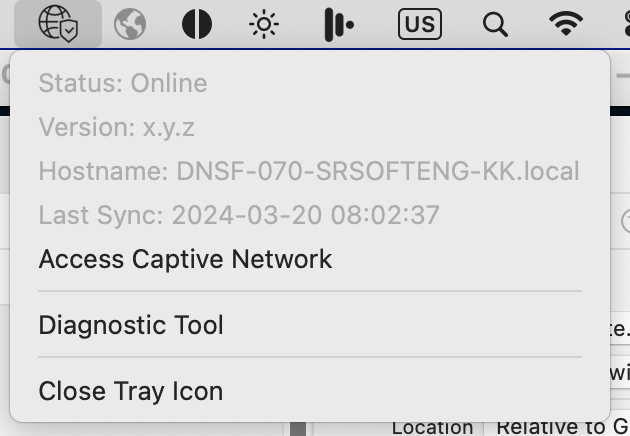
- After an extensive beta period aimed at improving compatibility with Captive Portal networks macOS RC v1.8.2 is now able dynamically handle all known types of captive networks. If the portal is not automatically opened you can use this new option in the menubar icon when connected to a captive portal that will trigger the page to open in a browser.
- A new configuration setting has been added to macOS RC to support excluding EDNS records for configured local domains. By default macOS RC does include EDNS records when resolving queries to local domains. However if these are creating conflicts for your users you can modify the behavior by installing v1.8.2 with this parameter set to false in the config file IncludeLocalResolversEdnsRecords=false
Bug Fixes 🪲
- Fixed issues affecting the Diagnostic Tool in previous versions that could result in the menubar icon crashing and/or incomplete log collection in the output zip file.
- Fixed an issue that could cause the roaming client to crash when attempting to sync local domains from the Dashboard that include capital letters.
improved
fixed
Web App
April 9, 2024 Dashboard App Release
Improvements 🛠️
- Insights Reporting breakdowns now use labels instead of icons for improved usability.
Bug Fixes 🐞
- Fixed a issue that could allow extra long organization names to distort the Org Selection menu for MSP and other Dashboard fields.
- Reduced extraneous reloads of the Geo Map on the Overview page that were updating as often as 1 sec.
improved
Mac Roaming Client
RC Release Channels
Apr 4, 2024 - macOS RC 1.8.2 Beta Release
A new version of the macOS RC is now available via the Beta channel. This version can be downloaded from the dashboard
Deployments
→ Roaming Clients
→ Install.
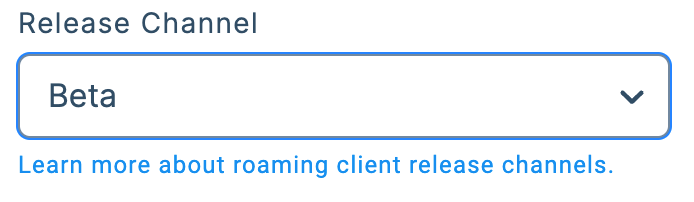
Additionally, your existing RCs can be configured to receive the Beta release via auto-update by modifying its Release Channel from Roaming Clients
→ Manage
.
For more details on Release Channels and the current versions available for both Beta and Production channels, check out our help docs.
Included in macOS v.1.8.2
Improvements 🛠️
- Continuing our improvements for captive portal compatibility, v1.8.2 is now able to more accurately detect when a network is preventing HTTP/S connections while not affecting DNS traffic. This should improve compatibility on the networks that still faced connectivity issues on v1.8.0 and earlier. Additionally, a new option in the menubar icon is now shown when connected to a captive portal that will trigger the page to open in a browser if the automatic mini browser does not open.
fixed
iOS Roaming Client
Apr 3, 2023 Release - iOS RC v1.2.0
A new version of the iOS Roaming Client has been released and is available for download in the App Store and will beginning rolling out via auto-update today.
Bug Fixes 🪲
- Fixed issue that caused connectivity to fail when on certain cellular networks with IPv6-only connections.
improved
fixed
Relay
April 3, 2024 Release - Relay v0.2.0
A new version of the DNSFilter Relay v0.2.0 is now available. Updated binaries can be downloaded from the Dashboard (
Deployments
→ Relay
→ Install
) and our Help Docs. VM images will be updated with v0.2.0 in the coming weeks.Improvements 🛠️
- Updated the behavior when Relay is configured with multiple local resolvers — previously, attempts would be made to each resolver in sequence leading to slow resolution times. In v0.2.0, unreachable resolvers are not attempted, speeding up resolution times. To get started with the new functionality, please see this new section in the Relay Deployment Guide
Bugs 🐞
- Fixed an issue that could cause the Relay to bind to port 5353 when configured to use port 53.
improved
Categorization
Popular Gmail domain changes
DNSFilter will be adding the
Webmail & Chat
category, in addition to the existing Business
category to the following popular domains:- googlemail.com
- m.gmail.com
This change is being done to better reflect the nature of these domains. DNSFilter will make these changes on Wednesday at 12pm (US EDT / UTC−04:00).
improved
Chrome Extension
Mar 27, 2024 Release - Chrome RC 2.3.0
A new version of the Chrome extension Roaming Client v2.3.0 is now available.
Improvements 🛠️
This version includes a behavior change when the Chrome Ext attempts to connect from a Chrome device or browser that is
unmanaged.
We've always recommended that our Chrome Ext be used on only managed devices due to the end user of an unmanaged device being able to easily remove or disable the extension. However, in previous versions of the Chrome RC, when connections were attempted on an unmanaged device the extension would register with DNSFilter as a new device with an empty hostname, leading to unwanted clutter in the Dashboard. In 2.3.0, Chrome RC will no longer registry as a new device when run on an unmanaged, making
managed devices required to run DNSFilter's Chrome Extension
.fixed
improved
Web App
March 19, 2024 Dashboard App Release
Improvements 🛠️
- Our latest machine learning model, Malicious Domain Protectionis now enabled in "Your First Policy" for new users.
- Tweaked the UI of the Dashboard's sidebar menu to make nested menus more clear and easy to navigate.
Bug Fixes 🐞
- Improved the usability of the domain filter on Insights reporting (Reporting->Insights) by waiting for multiple characters to be entered before loading data.
- Fixed a display bug on Filtering Schedules that weren't correctly updating assignments for a Collection.
- Fixed a bug when attempting to add an entry to a Universal List that would close the input window and require a second attempt to complete the action.
fixed
Windows Roaming Client
RC Release Channels
March 8, 2024 - Windows RC v1.13.0 Beta and v1.12.1 Production Releases
A new version v1.13.0 of the Windows RC is now available in the Beta release channel for New Installs and Auto-Update. This version can be downloaded from the dashboard
Deployments
→ Roaming Clients
→ Install.
Auto-update will push out the new release to RCs in the Beta Release Channel within the next 24-72 hours. Please refer to our release status page for the latest available versions in both Beta and Production channels.
Today we have also updated the latest version in the Production channel with
v1.12.1 - this build only includes a refreshed installation certificate used for the auto-update capability and is otherwise identical to v1.12.0 released on
January 10th, 2024
. This will ensure roaming clients can auto-update to upcoming releases that will require the updated certificate. Included in WinRC v1.13.0
Bug Fixes 🪲
- Improved the reliability and resilience in setting the active local user when installing, restarting or switching users on the device.
- Fixed an issue when an RC configured to use IPv6 only (via Registry key value) connects to an IPv4 only network that prevented resolution.
- Improved handling of restoring previous DNS settings in scenarios where the RC fails to operate due to inability to bind port 53.
- Fixed issues resolving .localrequests when no local Resolver is configuration for the user - default behavior will now automatically resolve request to fallback settings of the network device.
- Improved detection of manual changes to network device DNS servers while RC is running, resetting DNS back to DNSFilter.
- Fixed a compatibility issue with using Hyper-V and Windows Sandbox simultaneously.
- Reduced the frequency of the RC querying the windows domain controller for retrieving local user details, this should reduce CPU load on the domain controller.
fixed
Web App
March 5, 2024 App Dashboard Release
Bug Fixes 🐞
- Fixed an issue on Data Explorer that did not correctly list data broken down by Collections
- Fixed a bug that prevented a user from selecting "No Policy" for an existing deployment. We recommend policies are always applied to support greater protection but allow no policy to be applied for testing/deployment purposes.
- Corrected an display issue on Insights reporting that could display a single datapoint for a 24 hour period instead of a detailed breakdown.
Load More
→
